Updated: February 17, 2026
Nation-state adversaries are actively targeting the Defense Industrial Base (DIB) right now — not theoretically, not someday. Russian-affiliated ransomware groups, Chinese APT actors, and Iranian cyber operatives continue to probe defense contractor networks specifically to exfiltrate Controlled Unclassified Information (CUI). The Department of Defense knows this, which is exactly why the Cybersecurity Maturity Model Certification (CMMC) has moved from a regulatory promise to a contractual enforcement mechanism embedded in active solicitations across every branch of the military.
If your organization handles FCI or CUI as part of DoD work and is not actively pursuing CMMC certification, you are not just behind on compliance — you are an open target operating in one of the most hostile cyber environments in the world.
This article covers what CMMC looks like on the ground in 2026, which contracts already require it, what the threat landscape demands of your security posture, and how defense contractors can build the technical and operational foundation needed to achieve and maintain certification.
The CMMC program did not emerge from bureaucratic instinct. It emerged from a documented pattern of failure. For years, defense contractors relied on self-attestation to demonstrate NIST SP 800-171 compliance, submitting scores to the Supplier Performance Risk System (SPRS) that were often inflated, incomplete, or entirely fictitious. Meanwhile, adversaries — particularly nation-state actors associated with China and Russia — exploited those gaps systematically.
Ransomware gangs operating with state approval have simultaneously pursued profit and geopolitical objectives, as seen with Russian groups specifically targeting defense contractors. For organizations handling CUI in defense supply chains, the threat actor's motivation matters far less than their capabilities and your defensive posture. SecurityWeek
The DoD's response was to shift from a trust-based self-certification model to one requiring verified, independently assessed cybersecurity controls. CMMC operationalizes that shift — making it contractually enforceable, measurable, and tied directly to contract eligibility.
More than 220,000 contractors and subcontractors, including small businesses, are now directly impacted by CMMC 2.0, codified under 32 CFR Part 170 and enforced through DFARS 252.204-7021. Accorian

This is not a future requirement. It is a present reality. Below is a representative sample of DoD contracts and solicitations published on SAM.gov in February 2026 that already include CMMC language as a condition of award:
2/6/2026 — Cylindrical Antenna – Phase B System Department of the Navy, NAVAIR — CMMC Level 2 (CUI) anticipated. Offerors may contest the level assignment with justification.
2/5/2026 — 3DH2-M O&TI Mapping Operations U.S. Army Geospatial Center & USACE — CMMC Level 2 (Self) minimum; C3PAO preferred for all systems handling CUI.
2/5/2026 — DFSP Hachinohe Transformer Replacement NAVFAC — Requires a current CMMC Level 2 Self-Assessment posted in SPRS prior to award.
2/4/2026 — Site Lighting Conduits at 5 LFs Air Force Global Strike Command — Current NIST 800-171 Assessment or equivalent required as a pre-award condition.
2/3/2026 — Ship Self Defense System (SSDS) Legacy NAVSEA — CMMC Level 2 listed as a core capability requirement.
2/3/2026 — IDIQ MAC for Submarine Support NAVSEA — Contractors must be capable of undergoing C3PAO assessment every three years.
2/2/2026 — Inert Warhead for RRPR Department of the Army — CMMC Level 2 or higher explicitly required prior to award.
These represent a fraction of active solicitations. Across the Navy, Army, Air Force, and Special Operations Command, CMMC language is appearing consistently — and the frequency is increasing as Phase 1 matures and Phase 2 approaches. Failure to meet the CMMC Level 2 requirement makes an offer ineligible for award — full stop. PreVeil
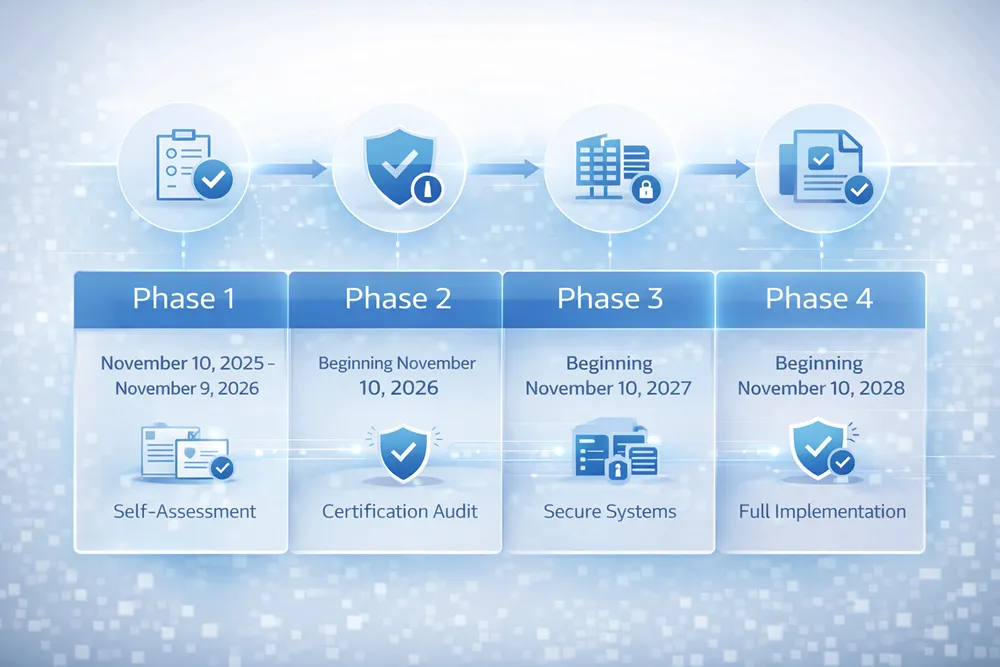
Understanding the phased rollout is essential for building a realistic compliance roadmap. Here is where the program stands today:
Phase 1 (November 10, 2025 – November 9, 2026) — Currently Active. Phase 1 of the CMMC program runs through November 9, 2026, and the DoD estimates that approximately 65% of the Defense Industrial Base will be affected. During this initial phase, the Department is primarily focused on self-assessment requirements rather than mandatory third-party certifications — however, some contracts may still require third-party certifications at the contracting officer's discretion. GovCon Wire
Phase 2 (Beginning November 10, 2026). Contracting officers will begin requiring C3PAO-assessed Level 2 CMMC status in applicable solicitations and contracts. Additionally, if the DoD so chooses, DIBCAC-assessed Level 3 CMMC status may be required. Morgan Lewis
Phase 3 (Beginning November 10, 2027). Level 2 certification requirements extend to existing contracts through option exercises. Level 3 DIBCAC assessments become mandatory for applicable high-sensitivity programs.
Phase 4 (Beginning November 10, 2028). Full implementation. CMMC clauses become mandatory in all applicable DoD contracts above the micro-purchase threshold where FCI or CUI is involved.
It typically takes 6–12 months to implement or remediate the NIST 800-171 controls required for Level 2, and some contractors with broader gaps may require up to 18 months. VC3 That math means that for Phase 2 compliance, the preparation window is effectively closed for organizations that have not already started.
A significant regulatory change took effect February 1, 2026 that restructures how contractors satisfy their assessment obligations. DFARS 252.204-7019 has been formally deleted, and DFARS 252.204-7020 has been renumbered to 252.240-7997. The self-assessment and SPRS upload requirements under the legacy 7019/7020 framework have been eliminated entirely. All assessment obligations now consolidate under DFARS 252.204-7021. DFARS 252.204-7012 remains in effect unchanged. This is not a minor administrative update — it changes the regulatory pathway through which contractors demonstrate and report compliance. If your organization's compliance documentation still references the old clauses, your SSP and SPRS submissions need immediate review.
Our managed security services include continuous regulatory monitoring to ensure your compliance posture reflects current DFARS requirements — so you are never caught off guard by rule changes like this one.
CMMC operates across three tiers, each calibrated to the type and sensitivity of information your systems process, store, or transmit.
Level 1 — Foundational applies to contractors handling Federal Contract Information (FCI). It requires 17 basic cybersecurity practices aligned with FAR 52.204-21 and is satisfied through annual self-assessment with results submitted to SPRS.
Level 2 — Advanced applies to contractors managing Controlled Unclassified Information (CUI). Contractors seeking Level 2 certification must implement the security requirements specified in NIST SP 800-171 Rev. 2. Assessment may be conducted as a self-assessment or by a C3PAO depending on the program office's determination. Certification at Level 2 is valid for three years, but contractors must submit annual affirmations to SPRS to confirm continued compliance. Alston & Bird Cloud service providers handling CUI must achieve FedRAMP Moderate authorization or equivalent.
Level 3 — Expert applies to contractors working on programs subject to Advanced Persistent Threat (APT) exposure. The SP 800-172 controls are intended for safeguarding information that may be the target of APTs — highly capable, resourceful, and patient cybersecurity threat actors generally associated with nation-states such as China, Russia, Iran, or North Korea. Wiley Level 3 assessment is conducted by DCMA's Defense Industrial Base Cybersecurity Assessment Center (DIBCAC) rather than a commercial C3PAO.
An important distinction: contractors cannot self-designate whether their CUI is prioritized. This determination is made by the DoD based on mission criticality, data sensitivity, and threat exposure. Accorian The level assigned in the solicitation governs your certification requirement — not your own assessment of the sensitivity of your work.
CMMC compliance is not an administrative checkbox. It is a direct response to ongoing, documented compromise of defense contractor networks. Understanding the threat environment your organization operates in is essential for prioritizing controls and allocating resources effectively.
Nation-state actors continue to target defense contractors to exfiltrate sensitive intellectual property, reinforcing the importance of verifiable cybersecurity practices across the DIB. SecureStrux The targets are not limited to large prime contractors. Small and mid-sized subcontractors — often with less mature security infrastructure — have become primary entry points for adversaries seeking to pivot laterally toward more sensitive DoD program data.
The CISA Known Exploited Vulnerabilities Catalog documents active exploitation patterns that directly affect contractor networks. Many of the vulnerabilities most frequently leveraged by nation-state actors against defense contractor environments appear in systems that would fall within a CMMC assessment scope — email infrastructure, VPN concentrators, remote access tools, and unpatched endpoints.
CUI spreads across cloud platforms, SaaS tools, endpoints, collaboration apps, and shared drives. Without automated discovery and classification, organizations face significant gaps in understanding their own exposure. Concentric AI That visibility gap is precisely what adversaries exploit — and what CMMC's 110 NIST SP 800-171 controls are designed to close.
For organizations that have not yet implemented the foundational controls around access management, incident response, audit logging, and configuration management, the threat is operational, not hypothetical. Our CMMC preparation services begin with a technical gap assessment that maps your current security posture against NIST SP 800-171 requirements and identifies the highest-risk control gaps to address first.
Technical controls address infrastructure vulnerabilities. But the human element remains the most exploited attack surface in defense contractor environments — and it is explicitly addressed in the CMMC control framework. NIST SP 800-171's Awareness and Training (AT) domain requires that organizations ensure all personnel understand the security risks associated with CUI, their specific role in protecting it, and how to respond to potential compromise events.
This is not a one-time onboarding requirement. It is an ongoing operational obligation that assessors scrutinize during C3PAO audits. Organizations that cannot demonstrate documented, recurring security awareness training with role-based components — particularly for personnel handling CUI — will find themselves with significant POA&M items that delay certification.
Comprehensive security training tailored to your organization's CMMC scope, personnel roles, and specific CUI handling procedures is a direct compliance requirement — and a critical layer of defense against the social engineering and phishing campaigns that nation-state actors routinely use to penetrate contractor networks.
One of the most consequential aspects of CMMC that many organizations underestimate is the executive accountability dimension. The CMMC program requires a designated senior official to submit annual affirmations to SPRS confirming continuous compliance with the applicable CMMC level requirements. That individual — typically a C-suite officer or equivalent — is making a legal attestation about the organization's cybersecurity posture.
False affirmations — including inaccurate self-assessments or executive affirmations — may trigger False Claims Act (FCA) liability, including fines and contract termination. Accorian The False Claims Act imposes treble damages and civil penalties on organizations that knowingly submit false certifications to the federal government. This is not a theoretical risk — the DoJ has pursued FCA enforcement actions against contractors specifically for inaccurate NIST SP 800-171 self-assessments.
This executive exposure creates a specific security challenge: senior officials attesting to compliance must be genuinely informed about the organization's security posture, not simply signing off on documentation they have never reviewed. Our executive protection services extend beyond physical security to encompass the digital and legal risk environment that executives navigate in high-stakes compliance and contracting contexts — including briefings on the cybersecurity obligations they are personally affirming.
Achieving CMMC Level 2 certification requires demonstrating implemented, documented, and operationally sustained controls across 14 security domains drawn from NIST SP 800-171. The domains include Access Control, Audit and Accountability, Configuration Management, Identification and Authentication, Incident Response, Maintenance, Media Protection, Personnel Security, Physical Protection, Risk Assessment, Security Assessment, System and Communications Protection, System and Information Integrity, and Awareness and Training.
For most defense contractors, the highest-risk gaps tend to cluster in a few predictable areas. Multi-factor authentication (MFA) implementation across all CUI-handling systems is frequently incomplete or inconsistently enforced. Audit logging and log retention — including the ability to reconstruct events and detect unauthorized access — is often immature. System Security Plan (SSP) documentation is frequently outdated, incomplete, or disconnected from actual system configurations. And incident response plans are often theoretical documents that have never been tested.
CMMC compliance depends on knowing what data exists before attempting to secure it. Organizations must demonstrate continuous control over where sensitive data lives, who can access it, and how risk changes over time. Concentric AI
A managed security service provider with specific CMMC expertise can bridge the gap between your current security posture and assessment readiness — providing continuous monitoring, log management, vulnerability management, and incident response capabilities that satisfy multiple NIST SP 800-171 control families simultaneously.
One of the most important mental models to shift when approaching CMMC is the distinction between passing a certification assessment and maintaining a compliant security posture. These are related but not identical objectives — and confusing them creates significant risk.
CMMC isn't really an end state. It feels like an end state, but it's really operational capabilities that matter. Organizations need to be self-aware of changes — acquisitions, divestitures, technology shifts, new data flows. All of these can impact your compliance posture. If you're not actively managing them, you're not ready. CyberSheath
Organizations that achieve Level 2 certification and then allow their posture to drift between the three-year recertification cycle are both non-compliant and vulnerable. The annual affirmation requirement exists precisely because DoD recognizes that cybersecurity is dynamic — new vulnerabilities emerge, personnel change, systems are modified, and threat actors evolve their tactics.
This is why the most defensible CMMC compliance programs are built on a continuous compliance infrastructure rather than periodic audit sprints. Our compliance-as-a-security solution model integrates regulatory compliance requirements directly into your operational security program — so that your CMMC posture is not something you achieve for an assessment but something you sustain as a living security discipline.
The formal Phase 2 deadline of November 10, 2026 understates how urgently the market is already moving. Major defense primes are enforcing CMMC compliance requirements on their supply chains independently of government contract language — and those requirements are binding on any organization that wants to maintain prime contractor relationships.
Lockheed Martin is requiring all suppliers to document their applicable CMMC status in SPRS and frames compliance as essential to maintaining uninterrupted business operations. For contractors handling CUI, the company urges them to pursue C3PAO certification now since some fiscal year 2026 contracts may already include that requirement. GovCon Wire
Boeing has issued similar directives to its supply chain, stating explicitly that suppliers handling FCI and CUI will be required to have the specified CMMC level certification identified in solicitations as a condition of contract award. Northrop Grumman has followed suit.
The implication is direct: if your organization depends on any of the major primes for a meaningful share of its defense revenue, waiting for formal Phase 2 enforcement to begin CMMC preparation is not a viable strategy. You will lose that revenue before the regulatory deadline arrives.

The path to CMMC Level 2 certification follows a consistent structure. Organizations that execute these steps systematically — rather than reactively — achieve compliance faster and with fewer assessment surprises.
Step 1 — Identify Your CUI and Define Your Assessment Scope. Map where CUI enters, moves through, and exits your environment. Every system, user, and process within that boundary is in scope for your assessment.
Step 2 — Conduct a NIST SP 800-171 Gap Assessment. Evaluate your current controls against all 110 requirements. Document deficiencies in your System Security Plan (SSP) and establish a Plan of Action & Milestones (POA&M) for remediation.
Step 3 — Remediate High-Risk Control Gaps. Prioritize access control, MFA, audit logging, and incident response — the areas most frequently flagged in C3PAO assessments. A complete System Security Plan (SSP), a Plan of Action & Milestones (POA&M) for any incomplete controls, and evidence showing implementation of each control are the core documentation requirements. VC3
Step 4 — Submit Your SPRS Score. Upload your self-assessment results and executive affirmation. Ensure your SPRS profile is current, accurate, and reflects actual implementation status — not aspirational compliance.
Step 5 — Engage a C3PAO Early. C3PAO schedules are filling rapidly ahead of Phase 2. Early engagement is not optional — it is a scheduling reality given current market capacity constraints.
Step 6 — Implement Continuous Monitoring. Establish ongoing log management, vulnerability scanning, configuration monitoring, and incident detection capabilities. These operational requirements must be sustained, not just demonstrated once.
Our CMMC preparation services walk your organization through each of these stages with the technical expertise and documented methodology needed to achieve a defensible, assessment-ready compliance posture.
At VisioneerIT Security, we're committed to safeguarding your business. Reach out to us with your questions or security concerns, and our team will provide tailored solutions to protect your digital assets and reputation.